End to End Automotive Cybersecurity: Development, Implementation and Support
Cutting Edge Solutions and Services for Automotive Cybersecurity
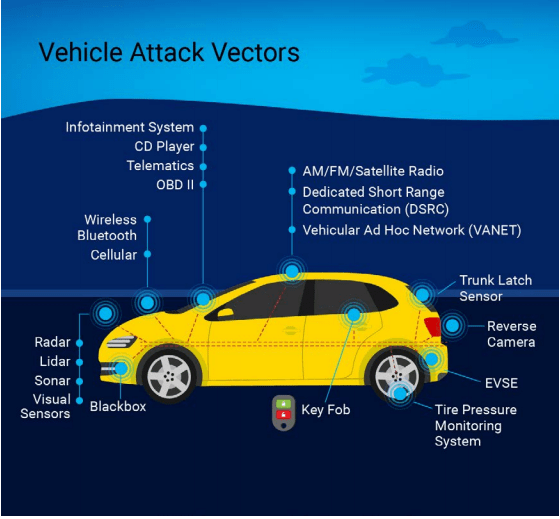
Securing a vehicle connected to multiple data sources over different networks is a technology intensive task. And a very crucial one at that! Each connected module in a vehicle is a potential entry point for cyber-attacks. We at Embitel, have delivered multiple automotive projects with cybersecurity at their core. So, we know where to put the plug! Automotive cybersecurity is all-pervasive, hardware, software, network, and cloud; we help you secure each one of them.
Automotive Cybersecurity Applications
Hardware Security
- Development of device drivers for built-in hardware security module (HSM)
- Secure boot and memory protection of the hardware modules
Software Security
- Secure ECU flashing through secure bootloaders
- Secure remote vehicle diagnostics over DoIP
Network Security
- Cybersecurity compliant communication protocols such as CAN, DoIP, J1930 etc.
- Secure communication between the vehicle and external infrastructure (V2V and V2X)
Cloud Security
- Secure over-the-air upgrades (FOTA)
- Secure authentication for data communicated to and from cloud
Customer Success Story: Flash Secure Bootloader Development
Business Challenge:
- Authenticity and integrity of the data to be flashed on automotive ECUs must be ensured to avoid mishaps.
- Solutions like ADAS, Telematics, Body Control Modules, etc. require secure Bootloaders equipped with features such as Digital Signature, Encryption, HMS and others.
Embitel’s Solution:
- We have developed secure Bootloader solutions for our customers based on their specific security requirements. Our bootloader solution comprises security features including AES-128, Digital Signature, CRC32, HMS Drivers, Secondary Bootloader (SBL). These components ensure that the inter-ECU data transmission is secure and data integrity is not compromised.
- AES 128 algorithm has been used for encryption/decryption of the image file. Data is secured using the AES 128 algorithm before sending it to the ECU from the flashing device.

Solutions and Services for Automotive Cybersecurity
Development of Secure Solutions
- We develop automotive solutions compliant with automotive cybersecurity standard (ISO 21434).
- Cybersecurity is ensured on all fronts- authenticity, integrity and confidentiality of data to be communicated.
- From inter-ECU communication to connectivity with external entities (V2X), FOTA etc, we develop solutions that are secure from all potential threats.
Cybersecurity Assessment
- Current maturity in cybersecurity practices is assessed.
- We perform a gap analysis to identify critical risks and their impact
- We build a security roadmap and execute activities related to automotive cybersecurity.
Cybersecurity Related Testing Activities
- Support for ISO 21434 recommended testing
- Qualified tools are used for verification and validation activities
- All vulnerabilities are identified, exploited and remedial solution is provided
Secure Bootloader
- Secure Bootloader solution is equipped with five security components- AES-128, Digital Signature, CRC32, HMS Drivers, Secondary
- Bootloader solution uses SHA 256 Algorithm for Digital Signature.
- Development of HSM device driver for the Bootloader Software to access the HSM module of the microcontroller.
Transport Layer Security
- Implementation of TLS module for secure communication between ECUs and remote flashing and diagnostics devices.
- We offer ready-to-deploy DoIP protocol software appended with TLS module for secure vehicle diagnostics.
- Development of Secure Firmware-over-the-air upgrade(FOTA) solution with TLS module
Why Partner with Us
1
Dedicated Team
A dedicated team of cybersecurity experts manages the project and closely monitors each activity
2
End to End Cybersecurity
Our automotive cybersecurity approach is designed to cater end-to-end cybersecurity requirements- from gap analysis to compliance
3
Successful Deliveries
We have delivered secure bootloader solutions, software stacks implemented with Transport Layer Security (TLS) module and state-of-the-art security algorithms

Related Blogs and Insights on Automotive Cybersecurity
Frequently Asked Questions on Automotive Cybersecurity
Ans: ISO 21434 standard has recently been published. However, our cybersecurity team has been closely following the various stages that the standard has gone through. Hence, we have a fair understanding of the standard.
We have been delivering cybersecurity related projects before the release of ISO 21434 standard, primarily based on its draft version. Since, the standard is now published, we follow the automotive cybersecurity guidelines as prescribed in the standard for all cybersecurity related projects.
Ans: Yes, we can make your existing automotive solution compliant to automotive cybersecurity. The process requires gap analysis and an assessment of existing cybersecurity measures. After the gap analysis, we will lay down the requirements and make changes in the solution. The changes might affect the entire system architecture, introduce new validation and verification methods and more depending on various factors.
Ans: Diagnosing a vehicle remotely has emerged as a convenient for the customer as well as the service center. But it also opens up a potential threat of unauthorized access to the vehicle function. We have a ready-to-deploy DoIP protocol software that enables remote ECU diagnostics. It is made secure by the Transport Layer Security module (TLS module) among other features such as Secure Socket Layer (SSL) and IP security.
Ans: We equip our Secure Bootloader solution with AES-128, CRC32, HMS Drivers, Digital Signature and Secondary Bootloader (SBL) features. These components make sure that that the data transmission between ECUs is completely secure.
A snapshot of our Flash Bootloader’s security features:
- Cybersecurity is implemented as per the project’s requirement and in case of an ISO 26262 compliant project, the ASIL grade assigned to the solution.
- Secondary Bootloader also helps in securing Bootloader software. follows the following sequence:
- Our secure Bootloader solution uses SHA 256 Algorithm for Digital. ECU validates this digital signature before downloading the image file for ECU flashing.
- Data Integrity is validated using CRC32, an error detecting code part of the platform software of the Bootloader solution.
- Few microcontrollers come with built-in HSM module that implements security for the Bootloader. We develop the HSM device driver for the Bootloader Software to access the HSM module of the microcontroller.
Ans: We have delivered FOTA solution to our customers with security features as required by the projects’ specifications.
Let’s look at all security features implemented:
- Code signing to ensure trustworthiness (data integrity & source authentication) of the firmware image to be updated.
- Integration of Wi-Fi/Bluetooth/GPRS/GSM modules for secure communication between the FOTA server and the target devices.
- Integration of the firmware with IoT protocols such as MQTT, CoAP; HTTPS & SSL for secure data exchange
- We have chosen specific encryption methods to check the sanity of the update package
Knowledge Bytes: Insights on Automotive Cybersecurity
Automotive cybersecurity is all about protecting the vehicle electronic components from unauthorized access and control. Growing degree of connectivity in vehicles creates avenues for amazing features. However, connectivity to external entities also makes the systems vulnerable to cyber-attacks. Automotive cybersecurity is a set of measures that can identify and thwart such attacks and keep the vehicle occupants safe.
Cybersecurity for road vehicles has been standardized in ISO 21434 standard. This standard defines the engineering requirements for managing the risks associated with cybersecurity. Right from the concept phase to component decommissioning, the standard has a framework for cybersecurity processes.
Automotive cybersecurity makes sure that the data transmitted to and from the vehicle ECU is delivered unchanged and to the intended party. To achieve this, three important aspects are controlled- Authenticity, Integrity, and Confidentiality.
Authenticity of the data implies that the data has been exchanged in a trustworthy manner and has been delivered to the intended receiver.
Integrity of the data means that the data has not been tampered with and the content is delivered unchanged and complete.
Confidentiality entails that there is encryption algorithm securing the data and to prevent it from being accessed and read by unauthorized recipient.